0x01 用大白话来简单说明 WAF 最基本的工作流程
1
| 捕获客户端的各种请求 -> 匹配WAF拦截规则 -> 命中规则后的处理动作 -> 将整个拦截过程记录到指定的日志文件中 -> 脚本绘制实时攻击图表
|
0x02 关于modsecurity
1 2 3 4
| 一款老牌的开源 WAF,相信经常搞渗透的朋友,对市面上经常用的几款WAF,都早已非常熟悉,废话不多说,咱们直奔主题 本次,我们只是单单把它部署到可用的状态,关于规则深度定制,绕过以及白名单设置是我们面的事情 个人非常不建议把modsecurity和nginx一起用,实际测试中,问题还非常的多,关于nginx更推荐用naxsi[后面再单独说] 至于源码包,可自行去 modsecurity 的官方站点下载 www.modsecurity.org
|
0x03 首先,先编译安装好基本的LAMP环境 [具体编译安装过程,可自行参考博客相关文章] ,这里暂时就直接用之前编译好的环境来演示
1
| httpd 2.4.27 + php 5.6.31 + mysql 5.5.57 + centOS6.8_x64
|
0x04 先停掉apache,因为等会儿要编译modsecurity生成对应的库
0x05 开始编译安装 modsecurity,一如往常,务必先装好一些必要的依赖库,不然中间会有很多的麻烦
1 2 3 4
| # yum install httpd-devel apr apr-util-devel apr-devel pcre pcre-devel libxml2 libxml2-devel curl-devel zlib zlib-devel openssl openssl-devel -y # cd modsecurity-2.9.2 # ./configure --with-apxs=/usr/local/httpd/bin/apxs 生成modsecurity的so # make && make install
|
0x06 在apache 配置文件中加载刚刚生成的modsecurity的库
1 2 3 4 5 6 7 8
| # vi /usr/local/httpd/conf/httpd.conf LoadModule unique_id_module modules/mod_unique_id.so 不要掉了这个库,否则你会发现一切配置都没问题,就是不拦截 LoadModule security2_module modules/mod_security2.so <IfModule security2_module> Include conf/extra/modsec.conf </IfModule> # cp modsecurity.conf-recommended /usr/local/httpd/conf/extra/modsecurity.conf # cp unicode.mapping /usr/local/httpd/conf/extra/
|
0x07 初步配置modsecurity,编辑modsecurity的主配置文件,激活modsecurity
1
| # vi /usr/local/httpd/conf/extra/modsecurity.conf
|
1 2
| 激活modsecurity,默认是处于关闭状态的 SecRuleEngine On
|
1 2
| 检查从post过来的数据 SecRequestBodyAccess On
|
0x08 下载编辑owasp-modsecurity-crs规则配置文件
1 2 3 4
| # git clone https://github.com/SpiderLabs/owasp-modsecurity-crs.git # cp -r owasp-modsecurity-crs/ /usr/local/httpd/conf/extra/owasp-modsecurity-crs/ # cd /usr/local/httpd/conf/extra/ # cp crs-setup.conf.example crs-setup.conf
|
1
| # vi /usr/local/httpd/conf/extra/owasp-modsecurity-crs/crs-setup.conf
|
1 2 3
| 默认只是记录到日志文件并不会拦截,所以我们需要将下面两行给注掉,下面两句话的意思很简单,其实就是当命中规则时,'auditlog'就是写到log中去,pass就是放过该请求 #SecDefaultAction "phase:1,log,auditlog,pass" #SecDefaultAction "phase:2,log,auditlog,pass"
|
1 2 3
| 开启拦截,和上面相反,当命中规则记录到日志的同时,再给客户端一个403 SecDefaultAction "phase:1,log,auditlog,deny,status:403" SecDefaultAction "phase:2,log,auditlog,deny,status:403"
|
0x09 加载规则,大家可根据自己的实际业务情况,针对性的开就可以了,这可能也是整个modsecurity最核心的地方了,里面包含了各种web漏洞攻击规则,各种攻击特征关键字,不过说实话,默认的规则还是远远不够的,而且还存在一些误杀问题,关于如何深度定制modsecurity规则,自己也暂时还在学习总结中,待理解透彻,会继续分享给大家,没事儿的话,大家可以好好规则里面到底都是什么东西
1 2 3
| # cd /usr/local/httpd/conf/extra/owasp-modsecurity-crs/rules/ && ll # mv RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf.example RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf # mv REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf.example REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30
| # vi /usr/local/httpd/conf/extra/modsec.conf include conf/extra/modsecurity.conf include conf/extra/owasp-modsecurity-crs/crs-setup.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-901-INITIALIZATION.conf Include conf/extra/owasp-modsecurity-crs/rules/REQUEST-903.9001-DRUPAL-EXCLUSION-RULES.conf Include conf/extra/owasp-modsecurity-crs/rules/REQUEST-903.9002-WORDPRESS-EXCLUSION-RULES.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-905-COMMON-EXCEPTIONS.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-910-IP-REPUTATION.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-911-METHOD-ENFORCEMENT.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-912-DOS-PROTECTION.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-913-SCANNER-DETECTION.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-920-PROTOCOL-ENFORCEMENT.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-921-PROTOCOL-ATTACK.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-930-APPLICATION-ATTACK-LFI.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-931-APPLICATION-ATTACK-RFI.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-932-APPLICATION-ATTACK-RCE.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-933-APPLICATION-ATTACK-PHP.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-941-APPLICATION-ATTACK-XSS.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-943-APPLICATION-ATTACK-SESSION-FIXATION.conf include conf/extra/owasp-modsecurity-crs/rules/REQUEST-949-BLOCKING-EVALUATION.conf include conf/extra/owasp-modsecurity-crs/rules/RESPONSE-950-DATA-LEAKAGES.conf include conf/extra/owasp-modsecurity-crs/rules/RESPONSE-951-DATA-LEAKAGES-SQL.conf include conf/extra/owasp-modsecurity-crs/rules/RESPONSE-952-DATA-LEAKAGES-JAVA.conf include conf/extra/owasp-modsecurity-crs/rules/RESPONSE-953-DATA-LEAKAGES-PHP.conf include conf/extra/owasp-modsecurity-crs/rules/RESPONSE-954-DATA-LEAKAGES-IIS.conf include conf/extra/owasp-modsecurity-crs/rules/RESPONSE-959-BLOCKING-EVALUATION.conf include conf/extra/owasp-modsecurity-crs/rules/RESPONSE-980-CORRELATION.conf include conf/extra/owasp-modsecurity-crs/rules/RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf
|
0x10 所有配置编辑完成后,重启apache,注意,这时候重启你可能会发现,中间有个小小的卡顿,mod的性能,哼哼……你懂的,如果只是单个站点防护,还是不错的,如果是……嘿嘿……
1 2
| # /usr/local/httpd/bin/apachectl -t # /usr/local/httpd/bin/apachectl start
|
0x11 实际的拦截效果如下
命令执行,具体拦截哪些命令其实都在它的rules目录下的.data文件中定义的有
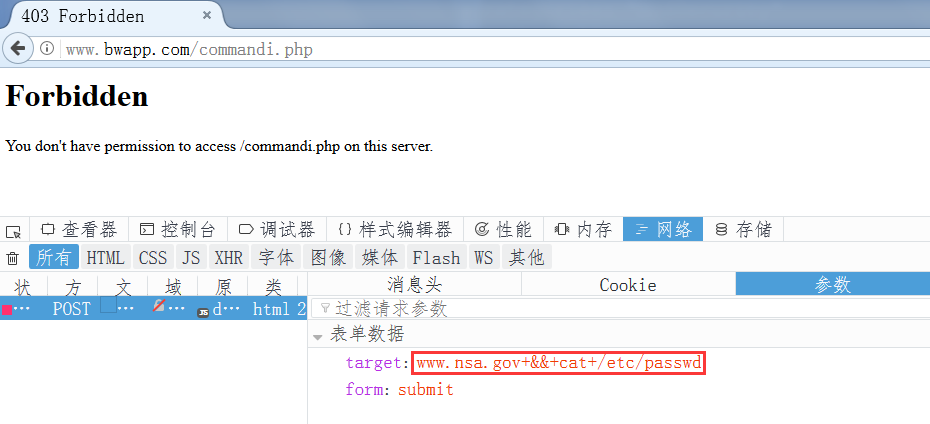
SQL注入,主要就是匹配各种数据库函数和sql语句关键字
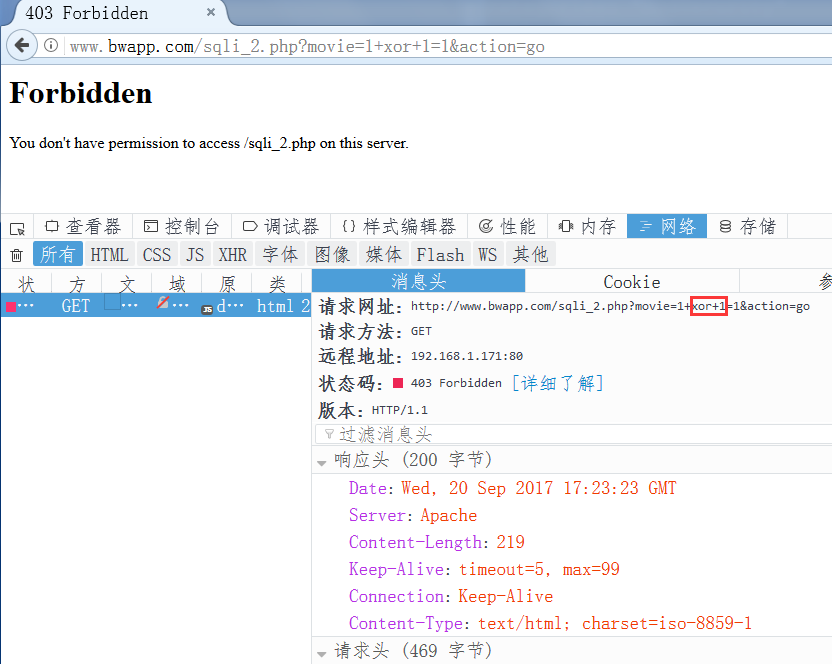
xss,就不用说了,能载入执行xss的标签,包括典型的js代码
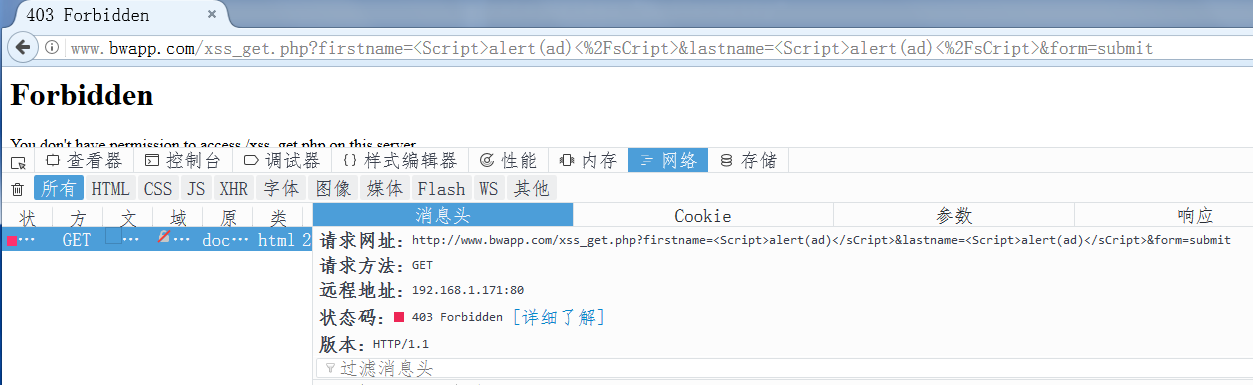
文件包含,其实,它可能就是在匹配像, ./ ../ 这样的路径分隔符
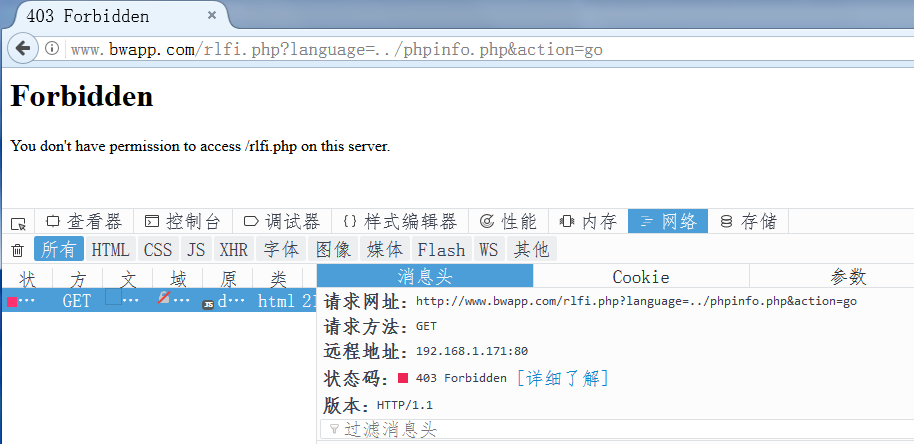
0x12 在日志中观察命中的各种攻击请求,其实,你完全可以把它用实时图表显示到网页上,根据不同的攻击类型动态绘图,形成类似的云WAF的效果
1
| # tail -f /var/log/modsec_audit.log
|
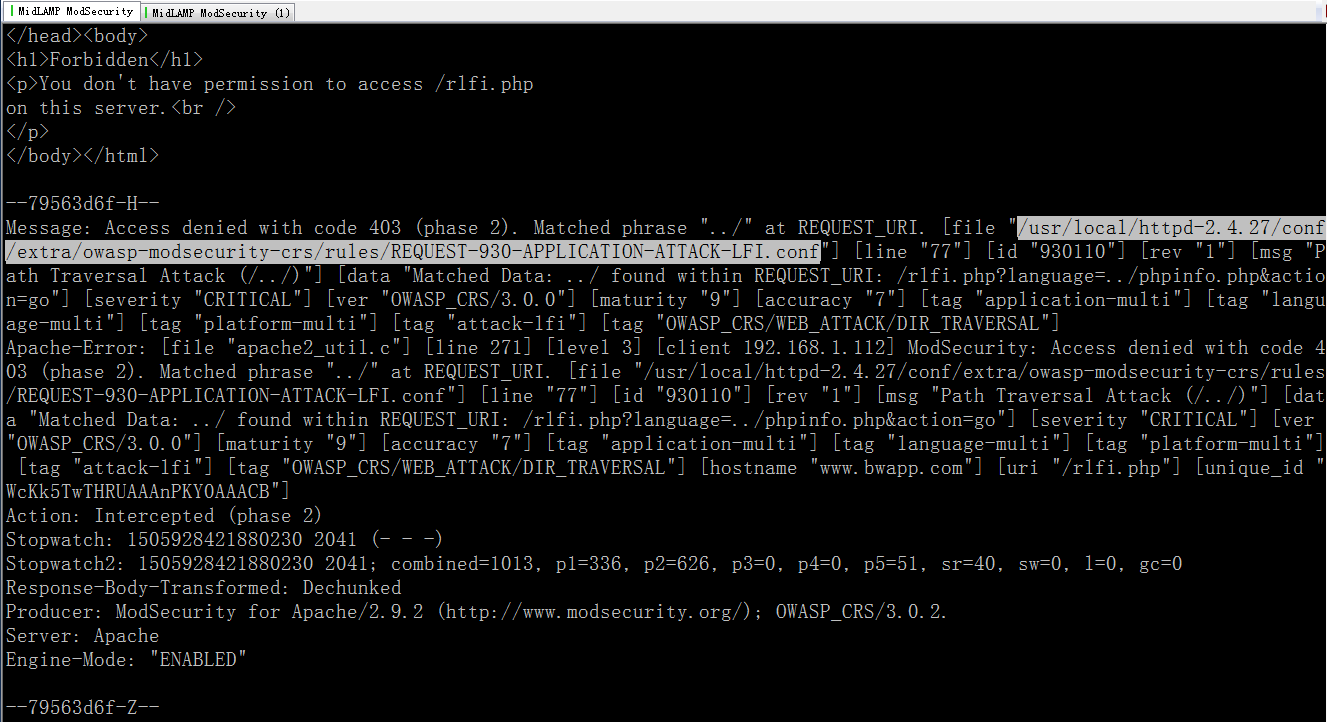
更多,待续……




